I recently needed to migrate my own personal Office 365 tenant to another Office 365 tenant and even though I only have a few fairly small mailboxes, I decided to use online migration tools to ease the migration and I thought it would be a good idea to put together a little comparison between two of the leading solutions, MigrationWiz and Dell (formerly Quest) On Demand Migration.
The truth is, migration tools aren’t new and many of today’s players in this market have been around for a some time. Cloud adoption however has driven innovation in the market and migration toolsets have changed in recent years. Online migration tools allow organizations to migrate their data between email platforms without having to install or maintain any migration software on-premises. From an IT professional perspective, the configuration is far simpler and because you are typically using a web browser to initiate and manage the migration you are now free to do it from wherever you want (the train in my case!) using whatever device you have available. At a high level, it is a fairly simple process which typically involves the configuration of source and destination connectors (with all the required permissions of course) and the solution will extract, convert and ingest your data for you. If either your source or target mail infrastructure is located on-premises, you would need to ensure that remote connectivity is correctly configured as well.
For this comparison, I used exactly the same source mailbox and migrated the content to two new target mailboxes (one for each tool) in a new Office 365 tenant. Both tenants (source and destination) were located in North America and the migrations did not run simultaneously. The source mailbox contained the following:
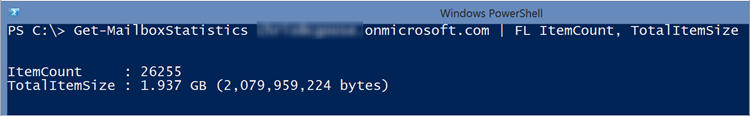
- Number of folders = 38
- Number of items = 26255
- Total mailbox size = ~1.94 GB
Introduction and features:
MigrationWiz has been around for a few years now and was the first online migration tool I used. I have successfully used MigrationWiz several times and migrated users from Domino/Lotus Notes and Exchange to Exchange or Office 365/Exchange Online. One of the great things about MigrationWiz is the amount of supported source and target platforms.
|
Supported sources
|
Supported targets
|
|
Amazon S3
Google Apps/Gmail
IMAP
Microsoft Exchange (2003+)
Microsoft Office 365
Microsoft Office 365 China
Novell GroupWise
POP
VMware Zimbra Server
IBM Lotus Notes
|
Amazon S3
Google Apps/Gmail
IMAP
Microsoft Exchange (2007+)
Microsoft Office 365
Microsoft Office 365 China
|
I should also mention that migrations from Domino/Lotus Notes require a small
“Lotus Extractor” to be installed on-premises. The extractor should be installed on a workstation and not your Domino servers themselves. MigrationWiz are also in the process of launching a new migration portal which is currently in beta and will support a couple of new migrations, namely:
- Public Folder migrations
- Storage migrations
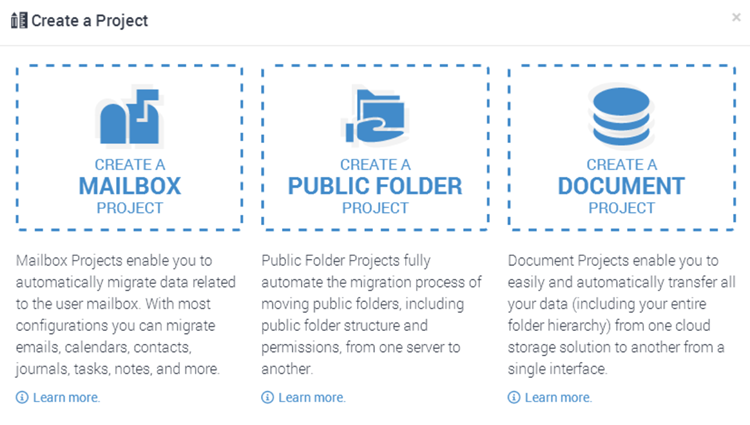
These options look really promising, however I haven’t personally tested them (yet!). A list of items not migrated by MigrationWiz can be found here.
Dell On Demand Migration for Email is a relative newcomer to the online migration tools market, however I’m sure we can all agree that they (Quest Software) really set the standard for migration tools in general for a long time. I haven’t personally used Dell On Demand for any production migrations but have been meaning to try it out for some time now. Dell On Demand supports the following platforms:
|
Supported sources
|
Supported targets
|
Google Apps
IMAP
Lotus Notes
Microsoft Exchange (2000+)
Microsoft Office 365
Novell GroupWise
POP
SunONE/iPlanet
Windows Live Hotmail
Zimbra |
Microsoft Exchange (2010, 2013)
Microsoft Office 365 |
Dell has published a list of known issues and limitations.
Licensing and cost:
One of the great things about both these tools is that they are licensed on a consumption basis and there is no minimum purchase required. MigrationWiz offers a couple of different license options, with the difference being that a “Premium” license will allow you to perform multiple migration passes. I usually suggest purchasing the “Premium” license because this works really well with the “seed and cutover” type migrations I usually perform with these tools. With MigrationWiz, you purchase you license up front and each successfully migrated mailbox consumes one of those licenses. Their licensing is based on volume so the more licenses you purchase, the more you save. A basic license will cost you $9.99 (USD) while a premium license costs $11.99 (USD).
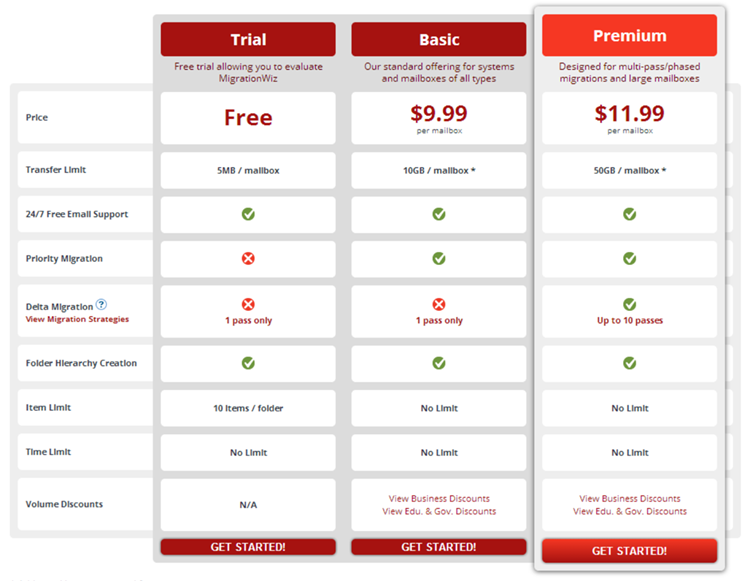
The Dell On Demand licensing model is somewhat simpler in the sense that they only have one license type. The difference is that you add your credit card details to the portal and they will bill you monthly for the amount of licenses you consume with each successfully migrated mailbox consuming one license and getting billed accordingly. Dell also appear to add an “Australia Tax” as the same license costs about 20% more when you pay in AUD, I always think this is a little cheeky, $1 or $2 could really add up if you are buying thousands of licenses. One license will cost you $11.00 (USD).

Configuration:
To configure MigrationWiz, you first create a “Mailbox Connector” which defines your source and target mailboxes as well as your migration credentials. You have the ability to use administrator credentials or end-user credentials configured per mailbox. If you have neither of these available, MigrationWiz also provides the ability to request credentials from each individual user. This is done via an email with a secure link in which the end-user may provide their credentials directly to the system.
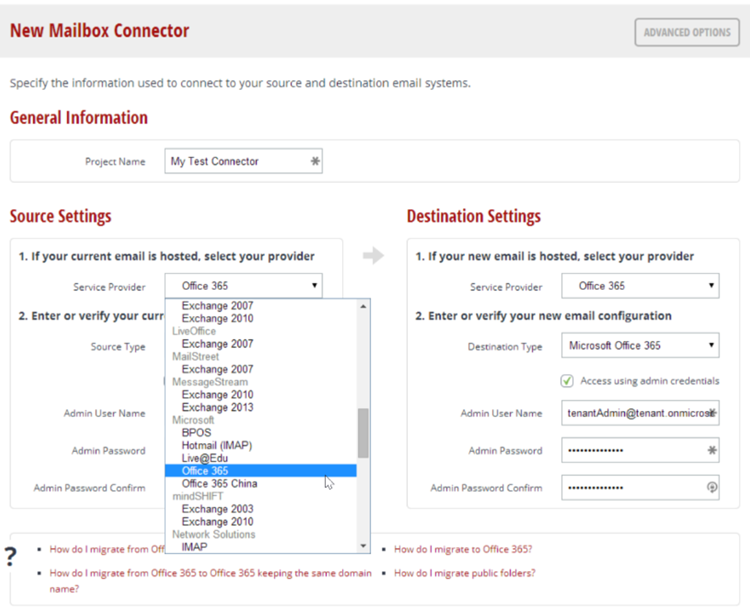
Once you have created your “Mailbox Connector” you can import your mailbox list. If you have more than one mailbox to migrate, MigrationWiz provides a few methods of doing this.
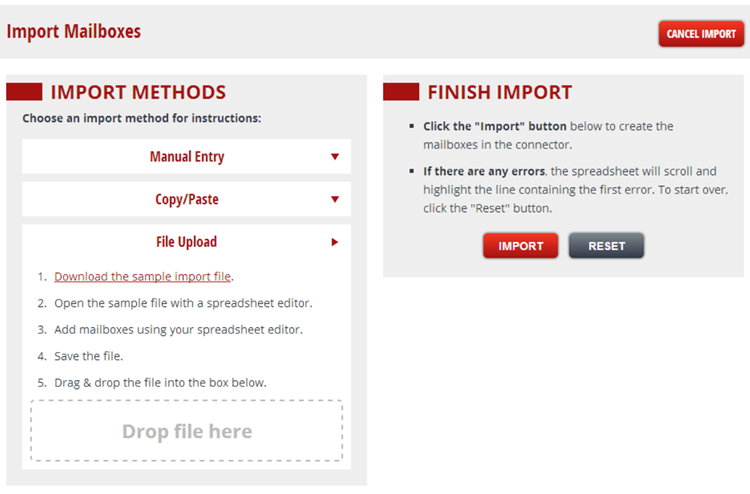
I typically use .csv import. You can download a sample import file to get started (see sample below). If you are using administrator credentials for your migration, you only need to populate the “Source Email” and “Destination Email” fields. More information about migration flags can be found here. I once did a migration for a customer using end-user credentials where some of the users had commas “,” in their passwords and needless to say, this didn’t work very well with .csv files so be mindful of that.
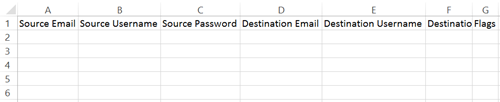
Once all your mailboxes have been added, you have the ability to tweak many of the migration settings, like filtering, before beginning the migration process.
You now have the ability to migrate a few or all of the mailboxes you have imported. You will also be able to monitor the migration statistics while the migration is running. The MigrationWiz documentation is really helpful as well, for example if you need more information about migration credentials, see this link
The Dell On Demand configuration process is very similar, you start by creating a “Migration Plan” which defines your source and target mailboxes as well as your credentials. You have the ability to use administrator credentials or end-user credentials and the tool allows you to increase the number of concurrent mailbox migrations by adding additional administrator credentials. Each administrator can migrate 10 target mailboxes concurrently.
The next step is to import your mailboxes, this can be done via a .tsv file. A sample file is also provided for reference.
The final configuration step allows you to tweak the migration options
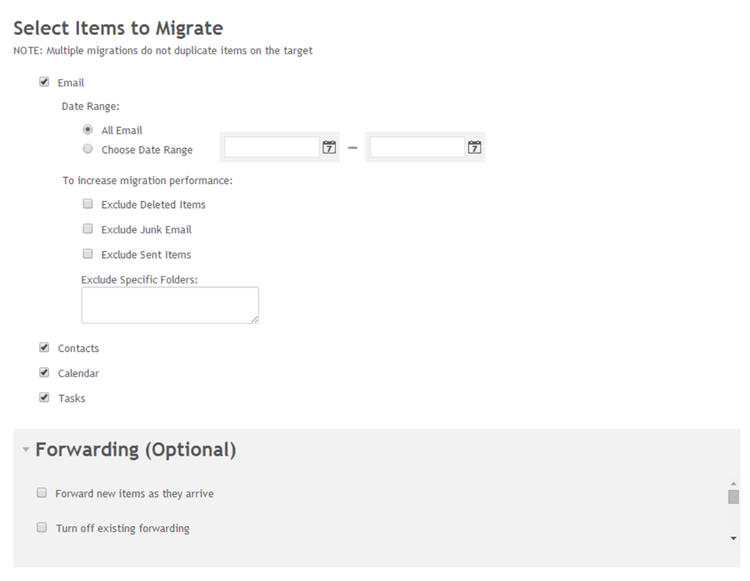
You are now ready to start migrating!
Migration Velocity:
As a consultant, one of the most common questions I get asked is “How long will my migration take?”. Unfortunately, this is a very difficult question to answer and the reality is, even with thorough testing and analysis, it is difficult to accurately predict how long a migration will take as every environment is different and migration velocity depends on so much more than just your network speeds. About 6 months ago, I helped a customer complete a migration from Exchange 2003 in one region to Exchange 2010 in another. They had a very tight deadline and it was a hard cut-off so there was no pushing the deadline. I did I whole bunch of calculations based on their source data size, connectivity, etc and in my mind there was no way we would be able to get all the data migrated in time so we started to prepare the business for that. We decided to use MigrationWiz for the migration and we ended up completing the entire migration with 4 full days to spare. Because we were prepared for the worst possible case, the entire team looked really good when we were able to pull it off successfully. I’m glad it didn’t end up going the other way and it just goes to show that there is always a small unknown factor that could change the amount of time taken for a migration to complete successfully.
It is usually a good idea to perform some test migrations using mailboxes that accurately represent those found in your environment. Using data from those migrations will go a long way to helping you predict your migration velocity. It is really handy to use some pilot user mailboxes for this because you will be able to perform multiple passes later on and not consume any additional licenses. MigrationWiz provides some guidance and a basic calculator here.
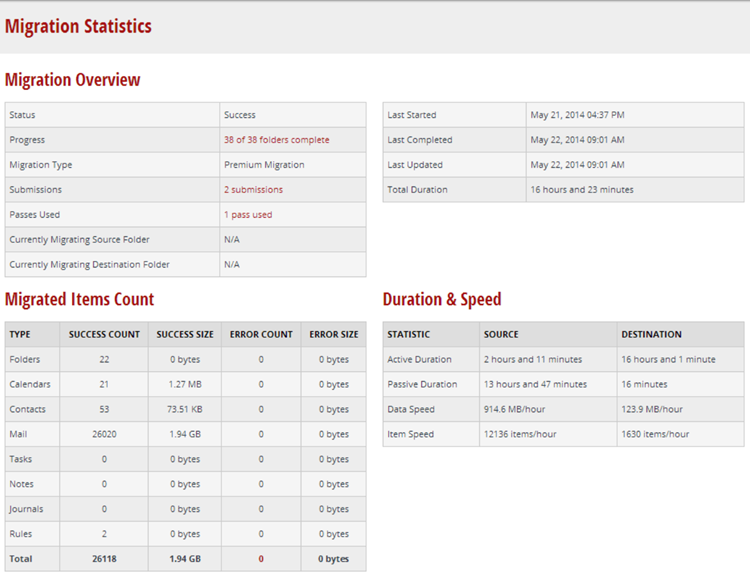
The results of the test migrations performed for this post are as follows:
|
MigrationWiz
|
Dell On Demand
|
| Duration |
16 hrs, 23 min |
11 hrs, 0 min |
| Items Processed |
26118 |
26286 |
| Errors |
0 |
13 |
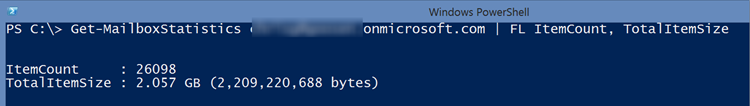
The statistics above were taken from each migration tool. There are some discrepancies with the amount of items processed and the Dell tool reported some failures. Looking at the target mailbox used for the Dell On Demand migration, we see:
MigrationWiz provides a whole bunch of information about the migration, including some detailed statistics:
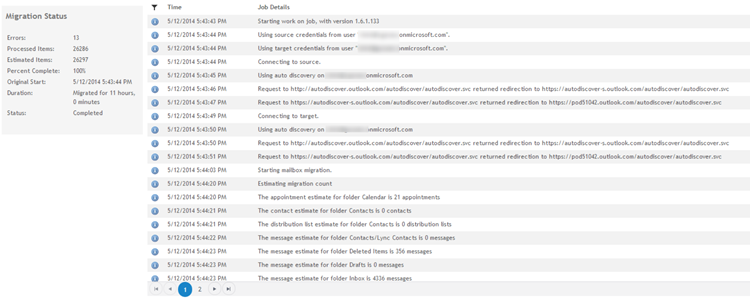
Dell On Demand provides an overview of the migration with some detailed logging:
I am perplexed by the large difference in migration duration. These migrations were run on random days of the week at roughly the same time so I’m not sure if it is a coincidence or not. I might re-do the MigrationWiz one sometime and see if it changes the duration.
Reporting:
MigrationWiz provides some nice charts at a mailbox level as well as some .csv reports at connector level for those who like to create their own reports in Excel.
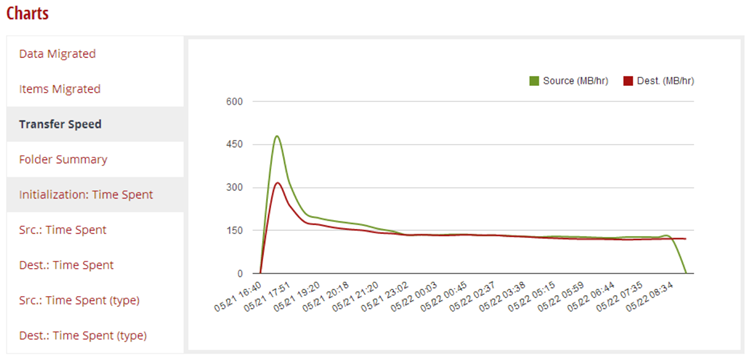
Dell On Demand provides a summary and a migration details report which includes a .csv file containing all the errors that were encountered during the migration. The reports menu is “conveniently” hidden on the bottom right-hand side of the dashboard.

Documentation:
MigrationWiz has heaps of useful documentation, the knowledgebase is located here: https://migrationwiz.zendesk.com/forums and it seems they are moving their content to a SharePoint based library located here: https://community.bittitan.com/kb/SitePages/Knowledge%20Base.aspx?product=MigrationWiz
Dell On Demand has a user guide which is published here: http://documents.software.dell.com/On%20Demand%20Migration%20for%20Email/1.6/User%20Guide/
In Summary:
I think both are excellent tools which provide a wide range of options. Dell On Demand is targeted towards those organizations who are migrating to Microsoft Exchange while MigrationWiz supports other target platforms, like the ability to archive to Amazon S3. MigrationWiz has also recently added the ability to perform Public Folder and Storage migrations. Dell On Demand appears to have outperformed MigrationWiz when it comes to migration velocity, however I do find the MigrationWiz documentation to be superior.