Moving from BPOS to Office365 – “550 5.4.1 Relay Access Denied”
With the recent launch of Office365 I was very excited at the thought of moving my existing BPOS account to a new Office365 tenant. I signed up, removed my “cgoosen.com” domain from my BPOS account and went through the process of adding it to Office365. I thought the whole process was going really well until I tested it by sending myself an email from another external account. I immediately received a “550 5.4.1 Relay Access Denied” error which seemed a little strange. After some research on the Office365 Community forums I realised that this seems to be a common issue with people moving a domain from BPOS to Office365.
I ended up calling Microsoft Customer Support and after some trial and error here is how I fixed it.
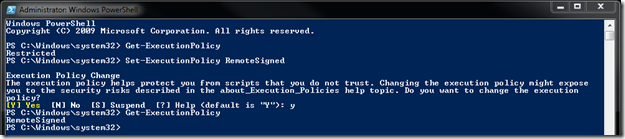
The first thing you need to do is use PowerShell to connect to your Office365 tenant, make sure you have the correct versions of Windows PowerShell and Windows Remote Management (WinRM) installed and configured on your computer. If you are running Windows 7 or Windows Server 2008 R2, you don't have to install anything. If you are running anything else, see the link at the bottom of the post. By default, PowerShell’s execution policy is set to “Restricted” that means that scripts won’t run so before we try to connect, we need to change that. Open PowerShell and execute the following cmdlets:
Get-ExecutionPolicy – verify that it is set to “Restricted”
Lets change it to “RemoteSigned”. PowerShell will now run any scripts that you write yourself and scripts downloaded from the Internet only if those scripts have been signed by a trusted publisher:
Set-ExecutionPolicy RemoteSigned
Now we are ready to connect to our Office365 tenant. Execute the following cmdlets:
$LiveCred = Get-Credential
Enter your Office365 admin credentials in the dialog
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell/ -Credential $LiveCred -Authentication Basic -AllowRedirection
Import-PSSession $Session
Once connected you, execute the following cmdlets:
Set-AcceptedDomain -Identity "yourdomain.com" -OutboundOnly $True
Set-AcceptedDomain -Identity "yourdomain.com" -OutboundOnly $False
You may need to allow around 40mins for replication, after that you should be able to receive mail again without the “550 5.4.1 Relay Access Denied” error.
If you are using running anything other than Windows 7 or Windows Server 2008 R2, see this link for information on Install and Configure Windows PowerShell.
For more information about connecting to Office365 via PowerShell, click here.